Digital security tips
Although nowadays most people associate the concept Big Brother with a TV phenomenon, the digital reality in which we are fully immersed might well refer to the prophetic intuition of the all seeing eye conceived by George Orwell in his novel 1984. We are living in a kind of glass house. Anything we do on the Internet leaves its trace. While we might think that our communications are secure, simply being connected means that many more people than we believe can gain access to our information.
TEXT JAVIER ORTEGA | ILLUSTRATION THINKSTOCK
In this “digital democratization” era, the percentage of citizens connected to the Internet is increasing daily. The universalization of Internet access has brought countless advantages, albeit accompanied by certain drawbacks. The greatest risk is the unbridled access to our information by third parties. To a large degree, preventing these uninvited visitors sneaking into our private life depends on each one of us.
There exist no foolproof methods, but you can start by raising your guard and eradicating that confident notion of those who believe these things always happen to others. The key is not to be afraid of making use of the digital resources at our disposal, but rather grow as responsible digital citizens, well aware of the need to take on board basic guidelines for using the Internet safely. This is the attitude companies should also adopt in order to deal with the inherent risks and endeavor to enhance the customer experience. For Guillermo Llorente, MAPFRE’s Security and Environment assistant general manager, “we cannot just ignore this reality; this situation is here to stay. We needn’t be worried, but simply take care.”
Options at our disposal
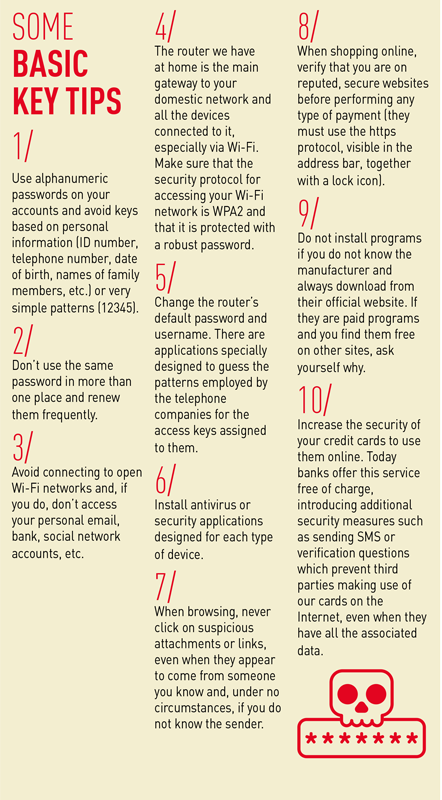
PC, laptop, cell phone, tablet, smart TV, smart watches… Our options when it comes to connecting to the Web are growing every day and, in parallel, the places where our private information is stored: our list of contacts, passwords for online banking services, email messages, photographs and videos, etc. First of all, we should fully understand the security options offered by each device we use to go online and, wherever possible, protect them with a security solution expressly designed for each of them, such as an antivirus or other specific security applications. It is also important to ensure our software and operating system (Windows, MacOS, iOS, Android, etc.) is always fully updated on each device, given that the most recent versions protect us from the latest security breaches detected. Not doing so can have consequences. In Spain, for example, one out of every four technical support cases handled under our insurance policies is related to problems with viruses and the installation of antivirus software.
With a quick look at your browser, you can check whether there are add-ons that you do not use, or simply do not remember having installed. In such a case, you should disable them. There are times when we download a program, press the OK button and, without realizing it, we are authorizing the installation of other utilities that often collect our browsing history or, in the worst case scenario, may be a way of introducing viruses or other malicious software (malware). Another elementary recommendation, which we generally only remember when it is already too late, is to make frequent backups of our device. If they are performed periodically, this practice can significantly reduce the risk of losing important data and information.
USE CAUTION AND COMMON SENSE
IN ORDER TO SPEAK OF HIGH SECURITY, IT IS RECOMMENDED THAT YOU USE AT LEAST 12 CHARACTERS THAT INCLUDE UPPERCASE AND
LOWERCASE LETTERS, SYMBOLS AND NUMBERS.
Online hazards
Even though the computer is where the need for online security seems most evident, these precautions may be applied equally to another types of equipment within our domestic ecosystem which have recently incorporated an Internet connection, such as smart TVs or game consoles.
Configuring security options does not end with our devices. Each app, most websites and, of course, all social networks (which we access in one way or another) have their own privacy settings (in the case of apps, the options area is often identified with a so-called cog or gear icon). Generally, we access this area the first time we enter a site or an application, but later forget all about it. It is not a bad idea to review the options there from time to time. Moreover, website privacy policies are constantly changing and, although they are required to warn us, it is important to review them.
Another fundamental aspect when it comes to protecting ourselves has to do with our passwords. In order to speak of high security, it is recommended that you use at least 12 characters that include uppercase and lowercase letters, symbols and numbers. You should not use the same combination in more than one application or device, given that, in the event of some vulnerability in a service resulting in keys being leaked (such as happened to Adobe) the pirates would have a much easier time.
Downloading pirated software or audio and video files, as well as being illegal, is one of the most common methods cyber criminals employ to gain access to our devices. The best way to avoid this is to not be a pirate. In the end, it all boils down to following a few basic guidelines which are equally valid for the offline world: above all else, use caution and common sense.
DID YOU KNOW THAT?
- IT TAKES 10 MINUTES TO HACK A PASSWORD WITH 6 LOWERCASE CHARACTERS
- IT TAKES 3 YEARS TO HACK A PASSWORD WITH 8 CHARACTERS, SOME OF THEM CAPITAL LETTERS
- IT TAKES 44,530 YEARS TO HACK A PASSWORD WITH 9 CHARACTERS, SOME OF THEM NUMBERS AND SYMBOLS